The landscape of self-protection for the Future Internet is extremely wide and as foundations for the research the Sotern team conducts, we advocate the following arguments:
- Self-protection can be enforced and be more efficient if the components involved integrate related mechanisms as an intrinsically embedded feature. This means that self-protection encompasses operational control loops but the components (or composition of) must have been carefully designed to limit their operational vulnerabilities to the soles that cannot be anticipated and rather exhibit intrinsic self-protection features.
- Self-protected communities may be of different natures. The set of target use-cases that may benefit from self-protection ranges from (1) cloud-based infrastructures counting millions of virtualized components to (2) spontaneous gathering of people in public places each owning IoT devices and taking part in a social service. As such, these communities require self-protection mechanisms to rely on scalable and resilient architectures, motivating the consideration of decentralized algorithms (e.g., detection, election, consensus) which intrinsically cope with the system features and avoid central-point weaknesses and threats.
- Self-protected communities must be considered as open and consequently not trustworthy. This means that the self-protection mechanisms must be resilient to undesirable behaviors and attacks that would compromise their own operation. As such, robust decentralized architectures such as blockchains will be considered among others as an essential infrastructure to ensure the integrity of self-protected operations despite adversarial communities and prevent, for instance, Byzantine attacks.
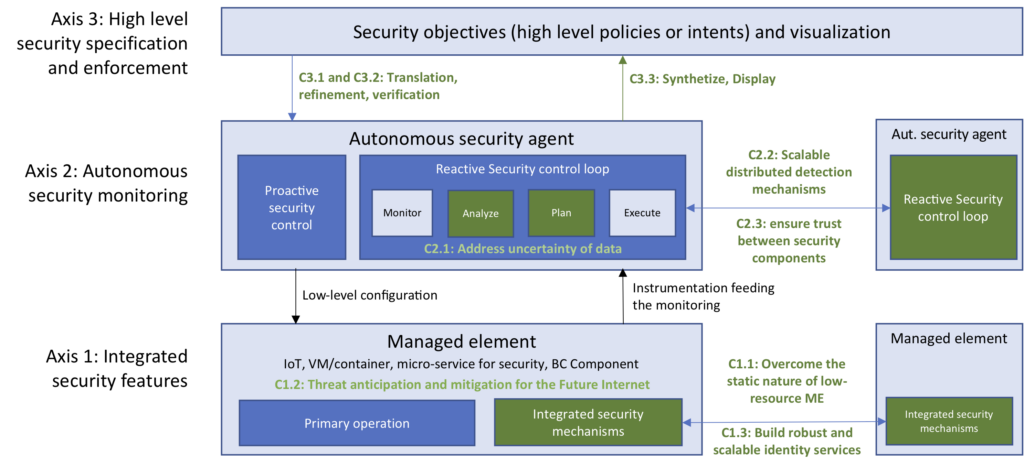
The above Figure depicts the overall scope of the Sotern team. It locates the different contributions in the scope of a self-protected system. Given the team statements exposed above, a first axis of research consists in designing components that intrinsically integrate security mechanisms which proactively protect them against external threats. As we subsequently describe, some relevant examples of activities conducted in the team regarding this axis concerns the design of Moving Target Defense strategies for the Internet of Things or the design of robust identity management systems leveraging the blockchain technology. Such use-cases are illustrative of situations where the self-protection does not require any external monitoring plane and it does intrinsically brings the expected security properties. Then, as the second axis of research of the Sotern team, we propose to address the situations where the self-protection must be provided by explicit monitoring components forming a self-protection control loop. Such a solution primary targets reactive security issues in which an attacker initiates malicious actions that need to be detected and mitigated. Finally, as a last layer required to also bring any supervised system with self-protection features, we consider in the third research axis of the Sotern team the need to conciliate the technical complexity of systems and the capabilities of people in charge of their monitoring and management. Here, we advocate that the intent-based networking, applied to security, is a key paradigm for future supervised systems and we explore and design solutions taking part in this paradigm together with some variants such as high-level policies. As a whole, the organization of the Sotern research axes are organized according to their “distance” from the target system, criterion which starts from embedded security mechanisms, then the design of explicit yet autonomous security monitoring solutions, up to objective-based system steered by humans.


